
Last year, thousands, possibly millions of people received rather disturbing emails. The emails took various forms, but all followed the same, basic structure. For example:
If you had been more careful while caressing yourself, I wouldn’t worry you. I don’t think that playing with yourself is very bad, but when all your colleagues, relatives and friends get a video recording of it – it is definitely bad for you.
I placed malicious software on a website for adults (with porn) which was visited by you. When the target taps on a play button, your device starts recording the screen and all cameras on your device begin to work.
So it’s your choice. If you want me to erase this compromising evidence, use my Bitcoin wallet address: XXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX
The Blackmail Email Scam of 2018-19 affected people all over the world (the exact number is unclear). Most people sussed out the scam for what it was, but, for many others, it clearly had an effect. Websites like Reddit saw plenty of traffic surrounding the emails, suggesting that thousands of people took them seriously enough to at least search online for answers.
Some people even paid the ransom. IBM tracked a series of Bitcoin wallet addresses involved in the scam, twenty of which had earned over $50,000. Check Point researchers found one wallet which received over $100,000 worth of Bitcoin in just five months of scamming.
Coronavirus Malware is Spreading
The Blackmail scam is a useful frame we can use to understand why, in the past three months, a slew of hackers have been leveraging the coronavirus towards their malicious ends.
Last month, the World Health Organization published a notice online: “Beware of criminals pretending to be WHO.” Hackers were leveraging the WHO brand to distribute malware-laced documents. In one case, a set of emails titled “Attention: List Of Companies Affected With Coronavirus” included a file labeled “SAFETY PRECAUTIONS.” Rather than a document, the label was actually an executable file, which downloaded a copy of the Agent Tesla keylogger to victim computers. A similar case making the rounds recently involves a file labeled “CoronaVirusSafetyMeasures_pdf.exe.” While clearly intended to be interpreted as a PDF document with information on COVID safety measures, it is in fact an executable which downloads the Remcos remote access trojan to a host machine.
These cases are hardly unique. In January, when COVID-19 was still relatively localized in East Asia, Japanese-language phishing emails were being used to spread the popular Emotet banking trojan. (Emotet, it should be noted, is a powerful malware with multiple dangerous capabilities. For example, Emotet-stricken computers are commonly rented out to criminal outfits for ransomware attacks.)
A new phishing campaign claiming to come from the Center for Disease Control is clever for a few reasons. Firstly, the hacker–whose IP address routes to the U.K.–effectively used a HELO command to mimic a .gov email domain. This adds an air of legitimacy that would be harder to convey with a non-government domain. Secondly, the link included in the email appears to direct to cdc.gov when, in fact, it redirects to a login page masking itself as Microsoft Outlook. Victims are baited into entering authentication information before being redirected to the CDC’s actual website.
These emails are perhaps even more impressive from a social engineering perspective. They mask the hacker’s intentions by providing real (unofficial) advice on prevention. And they play exactly into our worst fears, by claiming “three new cases have been confirmed around your location today.”
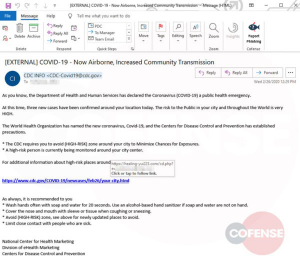
These fake CDC emails aren’t even the first fake CDC emails to leverage Coronavirus fears. Another, very similar campaign first observed in late January. It also used a fake cdc.gov link to redirect the unsuspecting to a fake Outlook login page.

Other similar cases include a campaign distributing the Lokibot under the guise of China’s Ministry of Health, and a three-page Coronavirus-themed document purported to come from Ukraine’s Ministry of Health which, in fact, includes macros that download backdoor malware with keylogging and screen capture capabilities onto a target computer. The latter case was particularly notable in its timing. Just a couple of days before it was spotted, violent protests erupted in Ukraine’s capital city of Kiev over a fake news story which also purported to come from the Ministry of Health, regarding an inbound flight to China that brought the virus to Ukraine.
Why We Click
Over half a dozen unique Coronavirus-themed malware attacks are making the rounds in the U.S., Europe and East Asia. While they differ slightly in approach and content, they all root from one, underlying truth: that humans are least rational when fearful.
Imagine if 2018’s Blackmail scammers, instead of purporting to have video of people masturbating, pretended to be marketers, job recruiters or Nigerian princes. Those Bitcoin wallets would’ve been far less active. The rational brain is overwhelmed by the primitive brain as soon as we’re confronted by personal threats, whether they be compromising videos or deadly diseases. Hackers regularly weaponize our own fears against us, because it works.
In all likelihood, hundreds or even thousands of people around the world today will follow fake Coronavirus links and files being spread by malicious actors. The best thing each of us can do is be vigilant. Consider whether the organization an email purports to be from would actually have your email address in their books. Scrutinize the name of attached files and links. Note that an apparently legitimate email domain is not in itself evidence of an email being from a legitimate source, nor is the use of an official letterhead or company logo.
If you’re concerned about phishing emails, but still want information on the virus, here are the legitimate COVID-19 websites maintained by the WHO and CDC:
https://www.who.int/emergencies/diseases/novel-coronavirus-2019/events-as-they-happen
https://www.cdc.gov/coronavirus/2019-ncov/index.html

About the author:
Nathaniel Nelson writes the internationally top-ranked “Malicious Life” podcast on iTunes, hosts programs on blockchain and SCADA security, and contributes to AI and emerging tech blogs.

