Guide to Intelligent Solutions for Privileged Access Management with Fudo Security NextGen PAM
Modern organizations face increasingly sophisticated cybersecurity threats, implementing ever-new solutions to keep business assets and user data safe, but rigorous and flexible privileged access management remains a key component. This guide provides security fundamentals, critical data, and expert advice for selecting the right PAM solution to help keep your data secure and simplify privilege management.

Why You Need This Guide?
Modern Cyber Threats. With the increasing complexity of network infrastructure and the number of endpoints, the security of privileged accounts is becoming a key priority. The guide offers solutions to protect against attacks related to unauthorized access and vulnerabilities such as excessive access rights.
Effective Privilege Access Management. Multiple accounts and the need to monitor them complicate business operations. Learn how modern PAM solutions can help automate privilege management and simplify auditing.
Meet International Security Standards. Stringent regulatory requirements such as GDPR and ISO 27001 require reliable access management solutions. This guide will show how PAM solutions can help you meet these standards and mitigate data security risks.
Download Your E-BOOK NOW!
To download fill up the following form:
What's Inside the Buyers Guide?

Key Cybersecurity Concepts. Learn about the data types to protect, key CISSP security domains, CIA triad principles, and the NIST framework that guides all cybersecurity lifecycle to build comprehensive defenses in the modern digital landscape.

Challenges and Statistics. Familiarize yourself with key vulnerabilities and their implications for modern enterprises, such as excessive access rights, lack of control over user actions, and inadequate account protection.

Components of PAM Solutions. Discover key PAM features such as privileged account inventory, credential management, and access control and learn how each plays a crucial role in protecting critical systems and data.

Challenges of Traditional PAM Solutions. Understand how traditional PAMs face challenges in managing access in hybrid cloud environments, implementation complexity, and lack of adaptation to new cyber threats.

Fudo Enterprise: Addressing the Challenges with Agentless Intelligent NextGen PAM. Discover how Fudo Enterprise solves critical problems faced by traditional PAM solutions by deploying in 24 hours, implementing Zero Trust and Least Privilege principles with a Just-inTime mechanism, minimizing access to critical systems, and providing advanced AI features to monitor and analyze privileged sessions and remote access.
Fudo Enterprise - Your Trusted Partner in Privileged Remote Access
Fudo Security is a recognized European leader in agentless intelligent solutions for privileged access management and secure remote access. Our AI-powered NextGen PAM solutions help companies effectively protect critical assets and help them comply with international security standards. We offer flexibility, security, and scalability so your company can stay one step ahead of modern cyber threats.
Download Your Guide Today!
Get full access to expert guidance and key data to help you choose the most effective and advanced PAM solution for your business.

Every third company has experienced a security breach in the last twelve months.
(source: 2023 Ponemon Institute Cost of a Data Breach Report)
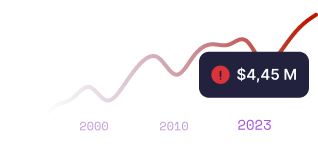
(source: IBM Security Cost of a Data Breach Report 2023)

(source: Cybersecurity Ventures)