ISO/IEC 27001 Decoded
Your Essential Guide to Elevating Security with PAM!
ISO/IEC 27001 provides a structured framework that organizations can follow to manage and protect information systematically. In this eBook, we outline everything you need to know about ISO/IEC 27001 and how to leverage PAM to meet its compliance requirements. Discover how specific Annex sections can be supported by PAM to strengthen your security posture and facilitate your path toward meeting compliance standards.

Why Download This eBook?
- Understand ISO/IEC 27001: Get a clear overview of the standard’s structure and requirements to understand what crucial risks to your business, company, and customers it is trying to guard against.
- Unlock the Benefits of PAM: Discover why Privileged Access Management is essential for protecting your sensitive information and see how PAM helps prevent unauthorized access and reduces security risks.
- Get Practical Strategies: Discover actionable tips for implementing PAM solutions that support alignment with ISO/IEC 27001, helping your access management practices contribute to meeting compliance standards and strengthening overall security.
- Stay Ahead of Compliance Changes: Learn about the future of ISO/IEC 27001 and PAM, and understand the upcoming trends in compliance and how to adapt your strategy accordingly.
Download Your E-BOOK NOW!
To download fill up the following form:
What’s Inside?

Introduction: Understand the importance of PAM in your security strategy and how it aligns with ISO/IEC 27001.

In-Depth Analysis: Detailed breakdown of ISO/IEC 27001’s requirements, including key objectives related to data confidentiality, integrity, and availability.

PAM Fundamentals: Learn PAM's main features and their critical role in safeguarding your information assets.

Strategic Alignment: See how Fudo Enterprise can help you meet ISO/IEC 27001 standards, providing efficient solutions that seamlessly integrate with your existing processes and multiple environments.

Looking Ahead: Insights into the future of PAM and the potential changes to ISO/IEC 27001 standards that could impact your compliance strategy.
Take Action!
Don’t leave your organization’s compliance to chance! Download “The Key to Compliance: Using PAM to Meet ISO/IEC 27001 Standards” today and equip yourself with the knowledge to protect your most valuable assets.
Join a community of forward-thinking professionals who are taking charge of their cybersecurity strategies!
Start Your Journey to Better Security
In a world where data breaches and compliance issues can seriously impact your organization’s operations and reputation, this eBook is not just another guide—it’s a practical resource for your business sustainability and success. Equip your team with the knowledge and tools they need to tackle the complexities of information security management effectively.

Every third company has experienced a security breach in the last twelve months.
(source: 2023 Ponemon Institute Cost of a Data Breach Report)
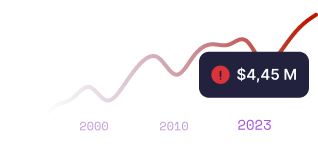
(source: IBM Security Cost of a Data Breach Report 2023)

(source: Cybersecurity Ventures)
 Download Our eBook Now!
Download Our eBook Now!