Download our exclusive ebook:
“How Privileged Access Management Can Help Your Company Achieve NIS2 and GDPR Compliance?”
In an era where regulatory landscapes demand heightened cybersecurity measures, Fudo Enterprise positions itself as your strategic ally. Learn how our solution, with features like proxy-based architecture and dynamic provisioning, not only ensures compliance but propels your organization ahead. Download now to gain a competitive edge, unlocking the benefits of seamless NIS2 adherence with Fudo Enterprise by your side.

Benefits of Downloading our eBook:
- Get acquainted with the fundamentals of NIS2, its scope, and directives.
- Learn how different sectors are categorized under NIS2 and the specific challenges they face.
- Explore how Privileged Access Management meets the technical requirements of NIS2.
- Understand the key aspects of GDPR and how PAM contributes to compliance.
- Discover how Fudo Enterprise offers a next-generation approach to PAM, specifically tailored for NIS2 and GDPR.
- Navigate the complexities of NIS2 and GDPR effortlessly.
Download Your E-BOOK NOW!
To download fill up the following form:
In this ebook:

Introduction to Privileged Access Management (PAM)

Introduction to NIS2: Scope and Directives

How PAM Meets NIS2 Technical Controls

GDPR Overview and Requirements

How PAM Enables GDPR Compliance

Fudo Enterprise for NIS2 and GDPR Compliance

Discover the Power of Fudo Enterprise in Cybersecurity Compliance
Discover the Key to Compliance Success
Unique Features for Streamlined Compliance: Uncover how Fudo Enterprise’s proxy-based access architecture and granular access policies simplify NIS2 and GDPR compliance efforts.
AI-Powered Security: Learn about Fudo Enterprise’s advanced threat detection and anomaly identification through AI-powered risk analysis, enhancing overall security measures.
Dynamic Access Provisioning: Explore the effectiveness of Fudo Enterprise’s just-in-time provisioning, providing temporary elevated access only when necessary.
Seamless Integration for Centralized Visibility: Understand how Fudo Enterprise seamlessly integrates with SIEM, DLP, and other security tools, offering centralized visibility crucial for compliance.
Download our eBook now to leverage these key aspects and pave the way for compliance success.
Ready to Strengthen Your Security?


Every third company has experienced a security breach in the last twelve months.
(source: 2023 Ponemon Institute Cost of a Data Breach Report)
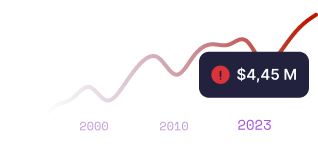
(source: IBM Security Cost of a Data Breach Report 2023)

(source: Cybersecurity Ventures)