Master USA Cybersecurity Compliance: Dive into our Exclusive CISO’s Guide Today!
Many companies face the challenges of complying with complex U.S. cybersecurity standards. This CISO’s Guide will help you understand the key regulatory requirements and their importance for securing your company’s infrastructure and customers’ data across different domains and regulators.

Why US Compliance Matters?
Compliance with U.S. cybersecurity regulations is not just a legal requirement but a must for business resilience and continuity. It helps protect your company from ever-evolving threats and build trust with users and partners by ensuring the integrity of data and infrastructure by complying with NIST, FCC, and HIPAA standards.
Download Your E-BOOK NOW!
To download fill up the following form:
What You Will Get From the eBook?
Explore critical compliance directives and frameworks:

NIST 8425: Learn the requirements for IoT products and systems, such as advanced identity and configuration management and protecting data from multiple sources across fragmented infrastructure.

NIST 800-53: Learn the requirements for managing privileged accounts and the comprehensive approach to access control, session monitoring, incident response, and auditing.

HIPAA: Learn the requirements for privileged access for healthcare systems with PHI data that demand stringent security measures such as role-based access control, multi-factor authentication, and session monitoring.

Fudo Enterprise - Your Trusted Cybersecurity Partner
Embark on a secure access management expedition with Fudo Enterprise’s turnkey cybersecurity solutions. Our Secure Remote Access and Privileged Access Management solution ensures intelligent access management and robust protection for servers, databases, and web applications.
Why Download?
Download our eBook to access clear and actionable insights about complying with NIST, FCC, and HIPAA requirements and take a proactive stance in protecting your organization from growing cyber threats and regulatory risks.
Claim Your Free eBook Now!
Take the first step towards cybersecurity excellence. Download our eBook today and fortify your business resilience and continuity in the ever-evolving landscape of cybersecurity compliance.


Every third company has experienced a security breach in the last twelve months.
(source: 2023 Ponemon Institute Cost of a Data Breach Report)
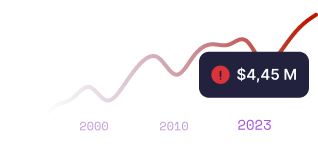
(source: IBM Security Cost of a Data Breach Report 2023)

(source: Cybersecurity Ventures)
 Download Our eBook Now!
Download Our eBook Now!