Fudo Enterprise:
Intelligent Secure Access!
The most comprehensive and secure infrastructure access solution.
Fudo provides the best protection for remote connections to Unix/Windows servers, databases, web applications, and network devices. With the Zero-Trust approach, users only have access to specific applications and accounts for a reason and when they really need it. Thanks to the proxy/bastion architecture, Fudo is a fully agentless product that you can deploy and start using the same day.
Used by thousands of users worldwide, Fudo is the perfect tool for managing access to your DevOps, Admins, Privileged Employees, Freelancers, Subcontractors, Vendors, and all kinds of third-parties.

$4.3M is the potential cost of a third-party related breach (Cost of a data breach 2022, IBM)

Main
Features
Agentless Convenient Access
Just in Time & SSO
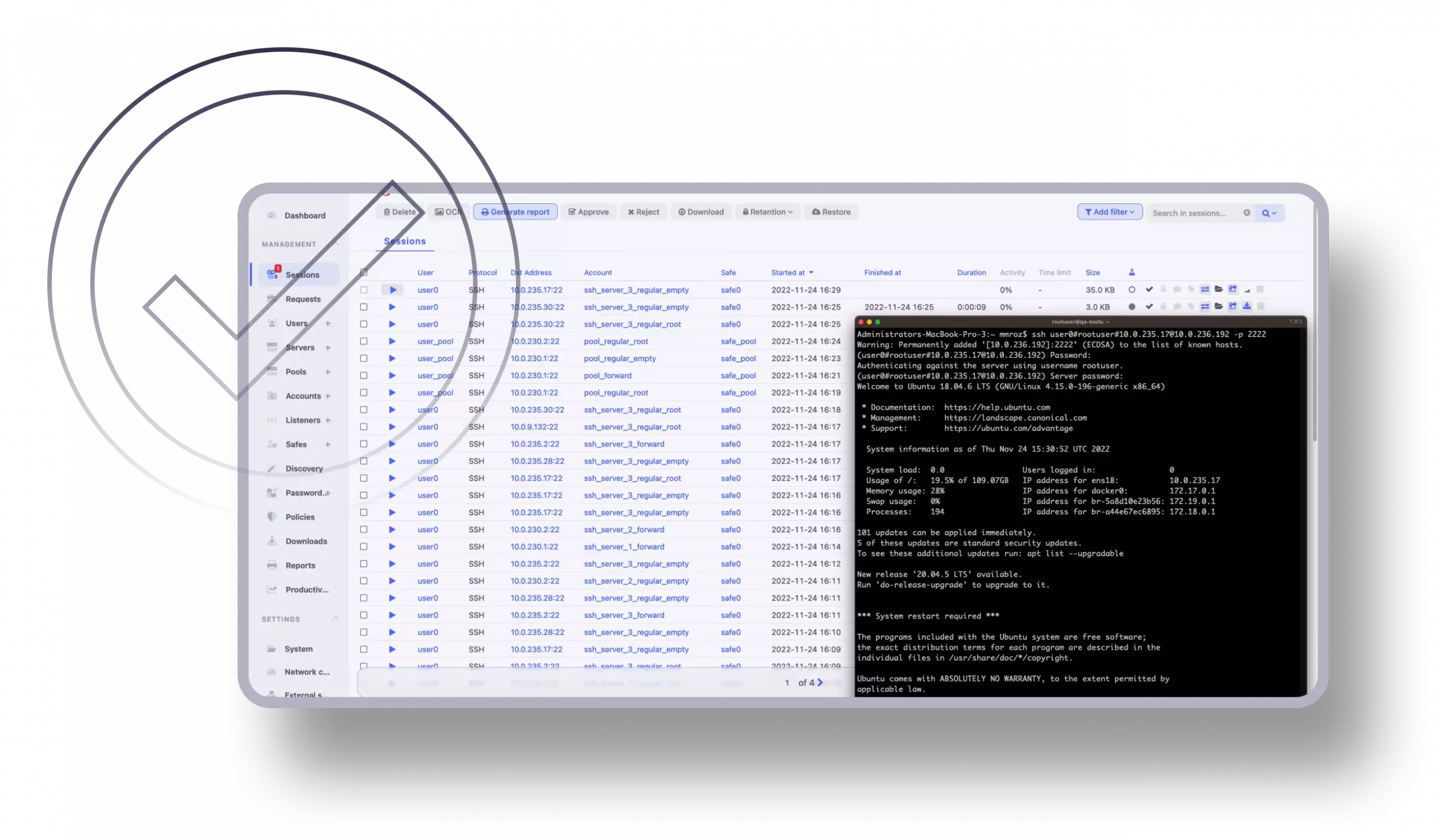
Session Monitoring & Recording
Secret Management
AI-Powered Prevention

Efficiency Analyzer
Rapid Deployment
Compliance
Fudo Enterprise helps organizations to meet compliance requirements: PCI-DSS, SOX, HIPAA, NIST, GDPR, ISA/IEC 62443.
USE CASES
Active monitoring and recording of sessions, with the possibility of joining and sharing each of them, allows for faster response time and appropriate actions conducted by CISO.
With AI schemes created individually for each user, administrators can easily track and narrow down any potential threat, wipe it out, and make a certain subject accountable for its actions. Policy assignment can passively trim users’ misuse by initiating a set of predefined actions from the system level.
The Forensic
Analyzer
USE CASES
centralized
remote access to
(Server) infrastructure
against
intentional and
unintentional abuse by
privileged users
of many
Administrators during
one session
The Forensic
Educational Use of
Sessions
Analyzer

Active monitoring and recording of sessions, with the possibility of joining and sharing each of them, allows for faster response time and appropriate actions conducted by CISO.
With AI schemes created individually for each user, administrators can easily track and narrow down any potential threat, wipe it out, and make a certain subject accountable for its actions. Policy assignment can passively trim users’ misuse by initiating a set of predefined actions from the system level.


