Secure Remote Access
Adapt to the digital transformation and connect your remote workforce securely.
The digital transformation has brought new obstacles for an emerging remote workforce and, with it, malicious attacks that target remote users. Organizations require visibility into remote user activity, authenticate and authorize users based on their need-to-know basis, and establish a secure connection between the user and the network infrastructure.
Practices such as Virtual Private Networks (VPN) or leveraging firewall policies for access management are often outdated and no longer able to secure remote access to critical resources. Moreover, with its encouraging use by a larger workforce, it offers attackers more targets to exploit and gain access to the network traffic, granting access to critical infrastructure resources.
Unraveling the Challenges


Secure Connection
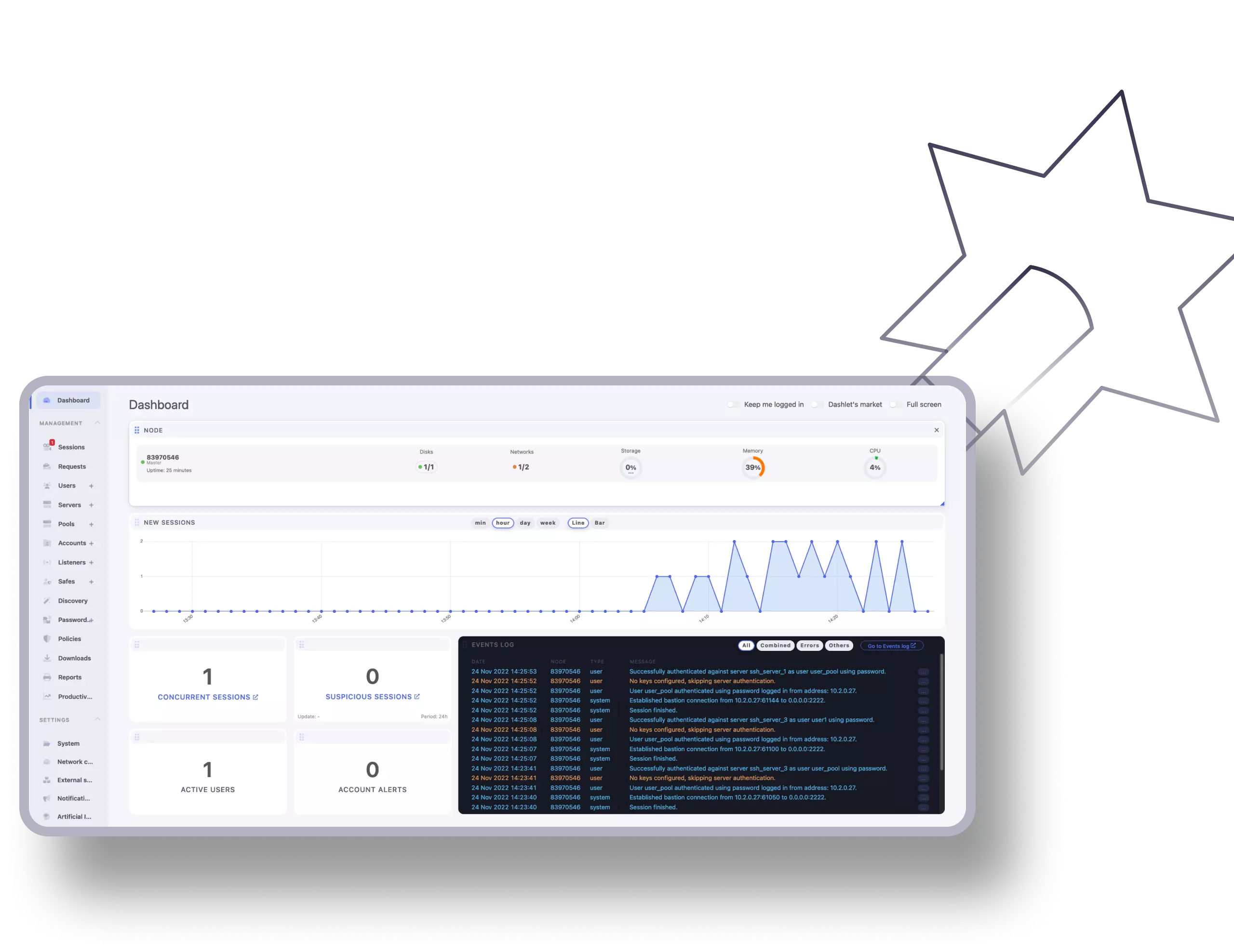
Fudo is located between the users and your network. Acting as a proxy and avoiding direct traffic to your infrastructure, Fudo offers over 12 protocol connections, from SSH, RDP, to VNC, and provides secure remote access in accordance with the Zero Trust philosophy. Allowing each user to connect securely to the resources directly from the Access Gateway.

User Activity
With active monitoring, each remote connection is monitored and recorded. Allows for video archive logs with full raw data processing. Enabling easier admin operations with the ability to intervene at any moment.

Authentication & Authorization
With several authentication methods (including passwordless certificates and MFA), Fudo enables a grid-like environment for privileged users. Enabling enough access to complete the task but obstructing any lateral movement within your network’s critical assets
BEST SECURITY
PRACTICES
Connect Securely Around the World
Secure Remote Access is now a necessity when it comes to remote operations, even when using on-premise connections. Businesses need to face new challenges that are emerging from the vast remote workforce and apply best-practice solutions to mitigate these cyber threats.
With Fudo Secure Remote Access, we enable full control of users and their connections. Administrators can monitor sessions to the most important system components and provide granular access to their environments.