Fudo provides the best protection for remote connections to Unix/Windows servers, databases, or web applications. With the Zero-Trust approach, users only have access to specific applications and accounts for a reason and when they really need it. Thanks to the proxy/bastion architecture, Fudo is a fully agentless product that you can deploy and start using the same day.
Used by thousands of users worldwide, Fudo is the perfect tool for managing access to your DevOps, Admins, Privileged Employees, Freelancers, Subcontractors, Vendors, and all kinds of third-parties.

$4.88M is the potential cost of a third-party related breach (Cost of a data breach 2024, IBM)

Main
Features
Agentless Convenient Access
With Fudo One, users can get access to their accounts quickly and easily. Users will not have to change their habits and can continue to use native clients. They can also connect through the Fudo Web Client which only needs a web browser for access.
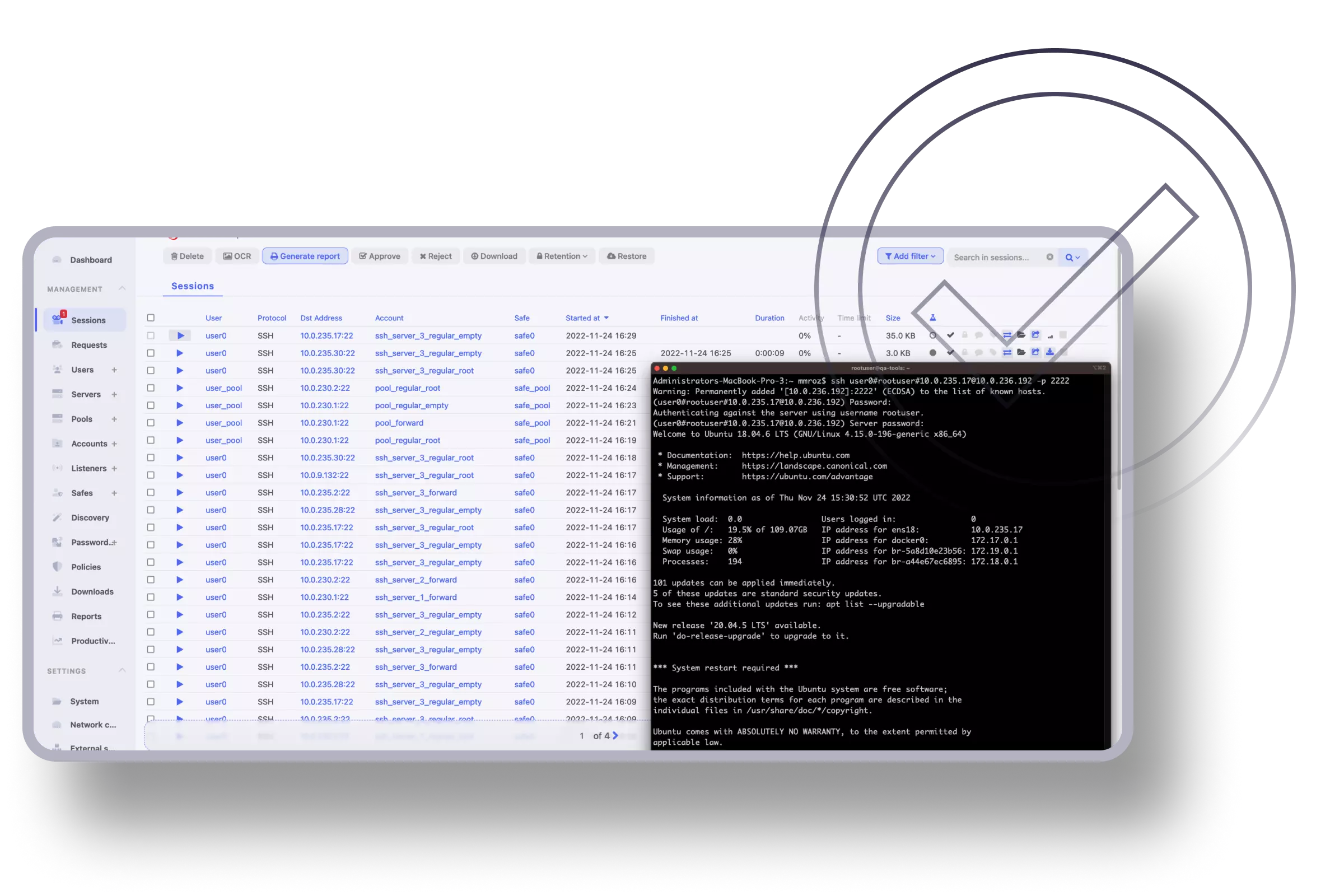
Session Monitoring & Recording
Now the administrators can control sessions with abilities to join, share, pause, or terminate any potentially suspicious session in real-time.
Share your resources over RDP, VNC, SSH protocols and record everything.
Super easy multi-factor authentication
Users can configure their own second-factor authentication methods by themselves. With the User Access Gateway, it is simple to set up mobile applications with OATH QR codes.

Quick installation
Through a single click, users can download software and start using their own Fudo One immediately.

Perfectly tailored
Fudo Security aims to provide secure remote access for companies of all sizes, from small businesses to large ones. Fudo One was created with the needs of small and medium businesses in mind, while Fudo Enterprise offers features ideal for larger enterprises with advanced IT requirements.
Compliance
Fudo One helps organizations to meet compliance requirements: PCI-DSS, SOX, HIPAA, NIST, GDPR, ISA/IEC 62443.
USE CASES
Through the User Portal, dedicated accounts can be easily and securely accessed using multi-factor authentication. The Web Access Gateway uses a built-in browser client for RDP, VNC, and SSH protocols.
Active monitoring and recording of sessions, with the ability to join and share sessions, enables faster response times and the taking of appropriate actions by the CISO.
Sharing sessions between multiple administrators enables better coordination of work while eliminating the need to use third-party software.
The Forensic
Recording sessions enable later analysis of the events and identification of the objects or persons responsible for violating security procedures. It is possible to search for keywords related to the incident.
Recordings of sessions can be a good source of information for in-house training of employees and, if work is carried out by suppliers, can be used to review the configuration prepared and executed by the contractor.
USE CASES
centralized
remote access to
Server infrastructure
against
intentional and
unintentional abuse by
privileged users
administrators
working together in a
single session
analysis
Using
sessions for
educational purposes

Through the User Portal, dedicated accounts can be easily and securely accessed using multi-factor authentication. The Web Access Gateway uses a built-in browser client for RDP, VNC, and SSH protocols.
Active monitoring and recording of sessions, with the ability to join and share sessions, enables faster response times and the taking of appropriate actions by the CISO.
Sharing sessions between multiple administrators enables better coordination of work while eliminating the need to use third-party software.
Recording sessions enable later analysis of the events and identification of the objects or persons responsible for violating security procedures. It is possible to search for keywords related to the incident.
Recordings of sessions can be a good source of information for in-house training of employees and, if work is carried out by suppliers, can be used to review the configuration prepared and executed by the contractor.


