What would you do if you woke up one morning, got out of bed, showered, made breakfast and, while you were eating your Wheaties, checked your bank account to find a couple hundred thousand dollars missing?
What would appear to be a comically exaggerated scenario was, in fact, a reality for one New York resident in 2012. This person fell victim to a particularly cutting malware, which took them for all of what it’d cost to buy a reasonably nice home in Albany. They were the exception to the rule, but their story–as well as the stories of other bank account breaches nationwide–can go some way to teach us how to avoid such worst-case scenarios ourselves.
Hacking Methods
As with cat-skinning, there’s more than one way to hack a bank account. The oldest and most reliable method is, of course, to steal a physical bank card. Digital methods are more diverse. For example:
- “Skimmers” implanted in point-of-sale machines and ATMs can read off the data encoded in a card’s stripe.
- Apps masking themselves as games or social media platforms on Windows-based app stores can hide malware on your device or siphon your PII to malicious actors.
- Hackers can plant themselves on a public WiFi network, waiting for an unprotected computer to make an unencrypted connection, then read off all the data that’s sent and received. If that computer’s owner is shopping online, that could include their payment information. If they’re checking their bank account, their login details.
It was a malware called Gozi, and an associated cybercrime online service called 76Service that caused that one anonymous New Yorker to lose $200,000 out of their account. They must have thought they were the unluckiest person in the world at the time, but two other victims of 76Service were reported to have lost a combined six million dollars to the same criminal outfit. Many, many more victims lost smaller amounts.
Gozi, more commonly referred to today as Ursnif, or its most common variant, ISFB, is one of an entire class of malware we call “banking trojans.” There’s Emotet, still very common as of this writing, and perhaps the most famous banking trojan, Zeus, responsible for siphoning a reported 70 million dollars from the innocent.
Deceptive Messages
Bank trojans, as the name would suggest, arrive on a victim’s machine masquerading as something other than what they actually are. A PDF included in an unsolicited email, a link in an SMS message from a number unrecognized. It is by virtue of opening these files (or, in even more sensitive cases, simply opening these emails) that the malicious payload masked within is able to download itself to your device.
It is because hackers have gotten so good at deception that these attacks are so effective. Take a 2017 case, where an unknown hacker or hackers began distributing emails to Canadian companies on behalf of their “banks.” The emails, and the malicious pages they redirected to, were highly detail-oriented. It’s easy to think “of course I would spot a fake email,” but check out the images below and consider honestly whether you’d think twice about what you see…
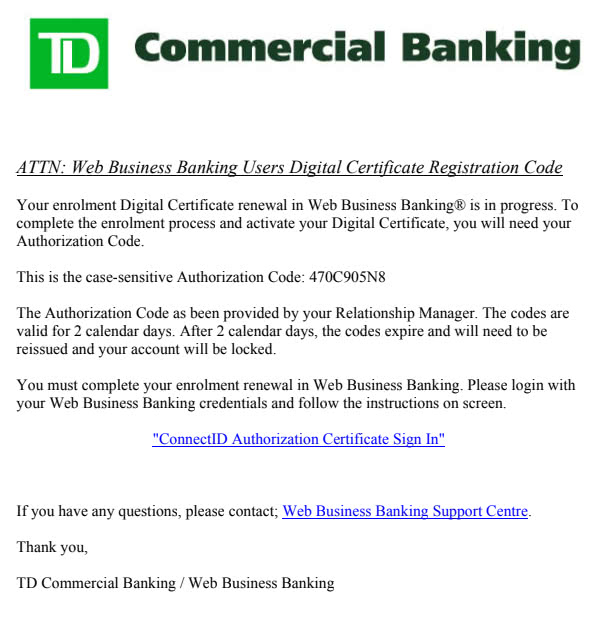
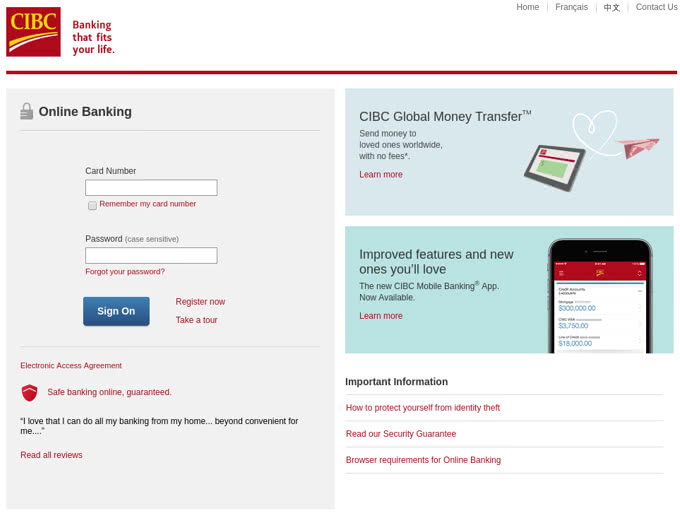
(Check Point Research)
Many of those targeted by the Canadian phishing campaign had no reason to suspect that they were falling into a trap. They willingly divulged their company’s bank information to the criminals who had only to sit back and wait.
Protecting Yourself
We receive so many emails every day that it’s hardly possible to carefully vet each one. We visit so many websites, use so many apps and interact with so many people that we can’t be expected to approach each individual cyber event with careful skepticism.
It’s why any solution to online financial protection requires a more thorough approach to cyber hygiene.
- Never open a link or PDF from a sender you don’t know.
- Tread carefully around websites you’ve never visited before, and download an HTTP Secure extension for each of your browsers.
- Avoid public WiFi where possible. If you can’t avoid it, at least avoid shopping online or checking your bank account until you get home. And use a VPN to encrypt your connection.
- Have a good antivirus program running on your computer at all times.
- Use long, complicated passwords for your bank accounts and change them as often as you’re willing to.
- Keep an eye on your account activity, and set up notifications to be sent to your phone every time a transaction is placed with your bank details.
- Take advantage of any other security protocols offered by your bank, like automatic fraud detection, voice recognition for phone calls, and two-factor authentication for online logins.
Even with all these measures in place, it’s not possible to be completely protected from all kinds of cyber threats. Just ask customers of Capital One who, last summer, learned that a lone hacker stole huge amounts of customer data straight from their bank’s online databases (luckily, FBI agents caught up to the perpetrator before any of it was released). If your bank is hacked directly, no amount of antivirus or two-factor authentication will save you.
What these cautionary measures will do, however, is make you less hackable than the person to your left, or to your right. Oftentimes, that’s more than enough. As they say: a gazelle in the jungle doesn’t have to outrun a hungry cheetah, it only has to outrun the slowest gazelle in its pack. Don’t be the slowest gazelle if it’s your money on the line.

About the author:
Nathaniel Nelson writes the internationally top-ranked “Malicious Life” podcast on iTunes, hosts programs on blockchain and SCADA security, and contributes to AI and emerging tech blogs.

